h3 headline 30 characters max
Donec rutrum congue leo eget malu suada. Praesent sapien massa, creallis sollicitudin malesuada euse consecturuer.


Join Google Cloud Security Leadership in Málaga for a two-day executive event featuring sessions from Google, Industry Partners and your peers.

days
hours
minutes



180 characters lorem ipsum dolor sit amet, consectetur adipiscing elit. Mauris id auctor erat. Mauris cursus pharetra purus, et blandit magna condimentum et felis.

days
hours
minutes
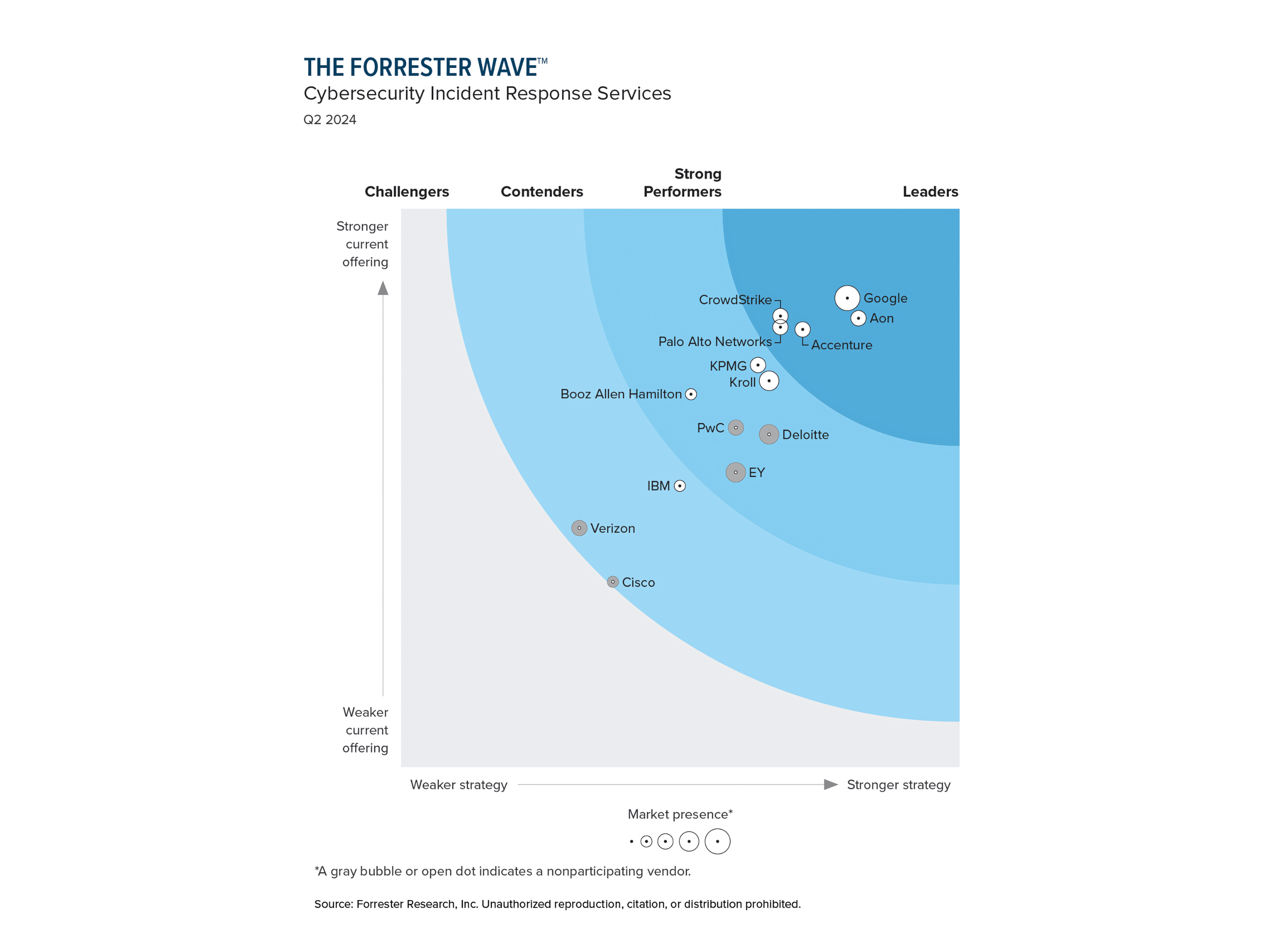
We are pleased to announce that Google was named a Leader in the 2024 Forrester Wave for Cybersecurity Incident Response Services. Mandiant, part of Google Cloud, designs and delivers services before, during, and after an incident.
Mandiant received the highest possible score in 17 out of the overall 25 predefined criteria areas.
We provide clients with rapid and effective detection, response, remediation, and long-term transformation services - and the scale of Google Cloud enables us to broaden our scope, increase our speed, extend our reach, and enhance our capabilities.
Finding the right incident response (IR) services partner is a key component for organizations to achieve cybersecurity resilience.
Read Forrester’s report to learn about:
120 characters autem quibusdam et autae officiis debitis aut rerum necessitatibus saepe eveniet voluptates repudiandae sint.
—Firstname Lastname, Title lorem ipsum dolor set amet
Security and risk leaders needing a provider fluent in technical, executive, regional, and regulatory communication that is on the front lines against complex adversaries and at the leading edge of threat intelligence, should look to Google," said Forrester in the report.
OPTIONAL EYEBROW
180 characters autem quibusdam et officii debitis rerum necessitatibus saepe eveniet quibusdam et officiis quibusdam et officii debitis rerum necessitatibus saepe eveniet quibusdam et officiis
Link textOPTIONAL EYEBROW
105 characters autem quibusdam et officii debitis rerum necessitatibus saepe eveniet quibusdam et officiis
Link textOPTIONAL EYEBROW
105 characters autem quibusdam et officii debitis rerum necessitatibus saepe eveniet quibusdam et officiis
Link textDate XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
Date XX, XXXX [SH-M]
Tracks available:
countries

VP, CISO
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud

Customer Engineer,
Google Cloud
Agenda subject to change
Donec rutrum congue leo eget malu suada. Praesent sapien massa, creallis sollicitudin malesuada euse consecturuer.
Donec rutrum congue leo eget malu suada. Praesent sapien massa, creallis sollicitudin malesuada euse consecturuer.
Donec rutrum congue leo eget malu suada. Praesent sapien massa, creallis sollicitudin malesuada euse consecturuer.
Donec rutrum congue leo eget malu suada. Praesent sapien massa, creallis sollicitudin malesuada euse consecturuer.
Donec rutrum congue leo eget malu suada. Praesent sapien massa, creallis sollicitudin malesuada euse consecturuer.
Donec rutrum congue leo eget malu suada. Praesent sapien massa, creallis sollicitudin malesuada euse consecturuer.

We hope you find The Forrester Wave™: Cybersecurity Incident Response Services, Q2 2024 report valuable.
After you read the report, browse Mandiant Incident Response Services.